
Most of us know security is important, but we still choose the lazy option when it comes to password security. Of course it's bad to use the same password for every website. But it’s not even good enough to use a strong password; we now live in a world where so much is tied up with our online lives that hackers are doing more and more to break into online accounts.
So, we’re going to look at the whole subject of password security, and hence online account security, how we can choose better passwords, how we can make our lives easier but also safer, how we can increase protection beyond passwords, and how hackers attack and use your account details.
Some of this advice you’ll have probably heard before, some of it is hopefully new, but by the end, you’ll be suitably terrified that you’ll overcome your human propensity for laziness, get up off your ass, and protect your passwords!
Let’s start by scaring you: There's been a host of research on password security, made much easier by the huge number of database breaches in recent years. One of the widest-ranging research efforts was by Google, published mid-2017 in its “Data breaches, phishing, or malware? Understanding the risks of stolen credentials” paper.
Some sweet nuggets from that little cache include the fact that the researchers swept over 1.9 billion non-unique account usernames and password credentials. These were taken from a variety of leak sources, but mostly blackhat security forums. An insane 76 percent of these could be (or already were) easily converted to plain text (best practice is to hash and salt stored credentials). The researchers were able to reverse an impressive 36 percent of hashed passwords, using a suitable keyword attack.
Of those stolen via phishing attacks, 49 percent were from Americans. When it came to pure security leaks, 39 percent of credentials were linked to Americans. As for credentials stolen via keyloggers, Americans were targeted in 8 percent of incidents; Brazil accounted for the highest amount in this group at 18 percent.
Credential leaks appear to happen regularly these days. The largest ever remains the initially hushed-up Yahoo leak, back in 2013, in which basically every single Yahoo account ever was leaked. Three billion in total. Adult Friend Finder topped 412 million, the 2017 Equifax breach hit 143 million Americans, while MySpace, Adobe, LinkedIn, Dropbox, LastFM, NexusMods, and many more have all had their leaks, each individually releasing millions of users’ details.
The biggest gaming news, reviews and hardware deals
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
These leaks show the basic issue with password reuse: If you are using the same password across all of your online accounts, it just takes a single leak and all your accounts are compromised.
Science save us!

So the logical next question is: What makes a secure password? Entropy. That means the level of randomness in a system. By randomness, we mean true randomness. It’s not enough to have a long password, it has to be long and truly random. We stumbled across a lovely analysis of poor passwords by WPEngine, which you can read here.
It’s worth a read—as well as being funny and interesting, it highlights a lot of general failings of humans when it comes to creating passwords.
The obvious beginnings are the standard bad passwords: “123456,” and any variation thereof, “password,” “qwerty,” and again any variation of those. Obvious stuff. Another issue is that many password guidelines are bad—forcing upper-case letters, for instance, because people tend to just capitalize the first letter; forcing at least one number, because people just put “1” at the end; or demanding a password of at least a certain length, because people use a pattern on the keyboard. For example, the seemingly random “ADGJMPTW” is actually people typing 2–9 on a smartphone number pad. This is what happens; it doesn’t make for strong passwords, because they’re easier to guess with a much lower entropy.
It’s that human nature thing. One group wants to protect a system, another wants an easy life, so it circumvents the rules, a third group is attempting to break in. So, how do we make stronger passwords?
A few years ago, a Dropbox engineer, Dan Wheeler, wrote a blog post referencing Randall Munroe’s classic XKCD correcthorsebatterystaple cartoon on password entropy, alongside Mark Burnett’s earlier research. Dan’s post is long and complex, and focuses on what makes a strong (high entropy) password, alongside how that can be easily measured and communicated to the user. Conversely, Randall’s point was part password strength, but he was largely extolling the need to make password systems human-friendly.
We don’t want to get into the nitty-gritty too much, but effectively a good password is a long password. Simple. The XKCD approach is to use a memorable series of words or phrase, usually painting an odd scene, such as the classic example of a “correct horse battery staple,” but it could be a phrase such as “basketball on a unicycle flying high.” From a memorable point of view, this taps into techniques used by memory experts. Throw in some numerals and symbols, and it’s even stronger.
None of this addresses the core issue, though, that we now have a seemingly endless number of online services to use and try, each with their own password and login. Even making passwords memorable wouldn’t solve the innate issue of having to remember them all. The solution to that is a password manager.
Microsoft save us!
The obvious place to start is to ask what tools Microsoft provides in Windows 10 and Windows 11. The blasé answer is none. Windows doesn’t come with any specific password management tool. What Microsoft has done is build a basic password manager into its Edge browser, which enables those saved passwords to be synchronized across your Windows accounts, and to any other instances of the Edge browser you might be running—Edge on Android, for example.
But what if you’re not on your Windows account? What if you’re not on Windows at all? What if you’re using Chrome or Firefox? What if you want to create a strong password? What if a site is demanding non-standard credentials? The Edge password manager is basic at best and fails to help in all but the most simple of scenarios.

Browsers save us!
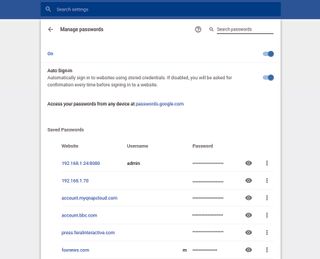
How about a browser that you might actually want to use? The most widely used browser is Google Chrome, and it comes with a reasonable password manager built-in. To kick-off, if you’ve logged in with your Google account, it syncs passwords across all of your devices and operating systems (Windows, MacOS, Linux, Chrome OS), and is, of course, available on Android and iOS devices, too. Google also offers an online service that enables you to log in and access passwords from within any browser on any device.
Beyond passwords, Chrome also supports intelligent form filling. You can enter a default address, phone number, and email address, and if Chrome thinks you’re filling those details in, it offers to try to autofill entire forms or individual elements. Alongside this, it has a secure credit card storage option, if you find the idea of Google having your credit card details a good one…. What could go wrong?
Chrome’s basic-but-smart-enough password manager means that as long as you’re logged in to your Google account, a right-click in a password field offers the option to generate a secure password. There are no options, it just provides a random password of suitable length. It then, of course, saves and manages that login and password for you. You can set exceptions and manage the saved passwords from within the “Advanced Settings.” Access to these is protected via a system prompt to enter your Windows password.
The other main browser worth a mention is Mozilla Firefox, although it doesn’t provide much more functionality than Microsoft Edge. It synchronizes your password across its own Firefox account to any supported OS or devices. It doesn’t support forms, won’t generate passwords for you, but does offer an independent master password to protect access.
LastPass save us!

So, browsers generally leave us wanting more when it comes to real password management. You could get by with Google Chrome, but we can do better. Enter the world of dedicated password managers. We’re going to concentrate on LastPass in this main section—for alternatives, see the various boxes throughout the feature. It’s certainly one of the prime options to look at when it comes to picking a password manager; the free account provides the majority of the basic functions people require, while the paid-for premium edition is just $2.60 per month.
LastPass is a multi-device, multi-OS, multi-browser tool. It largely works as a browser plugin for the big five: Chrome, Firefox, Safari, Edge/Internet Explorer, and Opera. It runs on all the main desktop OSes: Windows, macOS, Linux, and OpenBSD. And for mobile devices, there’s Android, iOS, and Windows Phone support. Plus, you can log in to your LastPass password vault through any browser, too.
The name LastPass comes from the fact that your LastPass account password will be the last password you need to remember; it’ll take care of all the rest. So, what does it do? The main use is via a browser plugin and apps on your mobile devices. As you create new accounts or login to existing ones, LastPass stores your usernames and passwords or offers to generate new passwords as accounts are created.
The LastPass password generator is pretty sweet. You can choose any length, up to 100 characters, select any mix of upper and lower-case, choose how many numbers to use, and decide if it should use symbols. There are also advanced options for avoiding ambiguous symbols or attempting to make them pronounceable.
Accounts can be grouped into categories and searched. You can add notes and opt for automatic logins, to help speed you into accounts. LastPass also supports automatic filling of standard forms: names, addresses, emails, phone numbers, bank accounts, credit cards, and custom fields. There’s a general encrypted notes tool, too. It also offers a warning for insecure forms, plus a security audit of existing accounts that you might import from your browser. Two-factor authentication is supported, too.
The paid-for service expands password filling to other applications, on both Android and Windows—LastPass can fill in a program’s password and fields; handy these days as more programs require some type of login for subscriptions. Once installed, it’s worth looking at the “Preferences.” We like to add a log-out time, so if you leave your PC alone, it logs itself out after an hour, for example.
LastPass isn’t the only password manager to offer all these features, but it does provide an idea of the expanded capabilities, improved security, and genuine ease of use a dedicated service offers.
But with great power, comes great responsibility. A service like LastPass requires you to use a strong master password; if that is hacked, someone will gain access to every service you use. Or if you forget the password, LastPass can’t restore your master password, as it is never sent in the first place, as a deliberate security measure. It might sound like we’re putting all our eggs in one basket, but what do you want—an individual basket for every egg or just one awesomely secure basket?
Even security-conscious businesses can be hacked and run into issues. LastPass has had a number of vulnerabilities exposed and even had a successful hack attack on its own servers in 2016. But as a security-conscious company should, LastPass offers bug bounties—which it honors—and is open about breaches with its users, while using best practices on its secure storage. So even the server breach in 2016 meant users’ own passwords remained secure.
Keep Steam secure
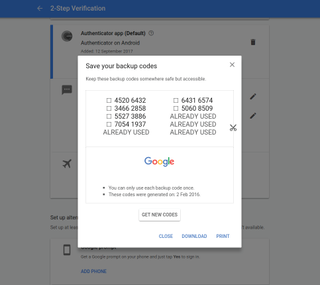
A question that security experts started to ask a while ago was: Is there anything better than passwords? You won’t like the answer, but it’s unlikely we’ll ever be completely free from passwords, though two-factor authentication offers a respite. Called TFA, or 2FA, for short, the premise is that people require two forms of identification, aka authentication; typically, the first is a strong password (something you know), and the second can be your fingerprint, your delightful face, or a generated one-time-use passcode (something you have).
As you might have spotted, many phones are now using fingerprints and face scans to authenticate access. Financial institutes are even happy enough that NFC-equipped phones can authenticate credit card transactions. Some systems (LastPass, VeraCrypt) accept USB thumb drives and specialist USB keys (Yubikey) as a second form of authentication.
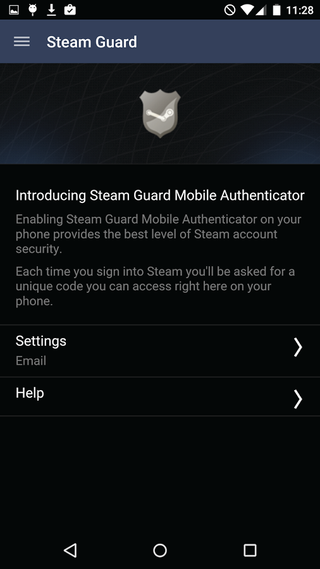
Steam is a good example of a service that was quick to provide two-factor authentication. You should be familiar with its email verification, which sends a code to your default email address. Valve also introduced the Steam Authenticator app, which is required if you’re messing around with its trades.
Alternate managers

We’re going to suggest three other commercial password managers—the ones that crop up most often, and generally offer similar features at similar costs. So, it’s down to you which you feel works the best. The first is 1Password.com; prices start at $2.99 per month for a single user and $4.99 for a family account for four people.
DashLane is a major player and offers a number of plans that will suit a wide range of consumer and business uses. The basic plan is free for all but is limited to working on a single device. The paid home plan is $3.99 a month, and supports unlimited devices, password sharing, and Yubikey TFA support. A business plan starts at $4 per user, and includes remote management, group sharing of passwords, and enhanced TFA options, among other things.
Our final option is Keepersecurity.com. It has a similar structure to DashLane, but opts to have yearly subscription pricing. The basic single-user package is $29.99, effectively $2.50 per month, and offers unlimited devices with sync, unlimited password storage, secure cloud backup, fingerprint access, and web access with support. A family option costs $59.99 for five users. there are, of course, a host more password managers. You can find a vaguely independent list on Wikipedia, or our sister website techradar maintains a list of free(ish) password managers.
The open-source way
We like open-source; it might not always produce the most polished-looking software [cough] GIMP [cough], but for security software, its publicly scrutinizable code tends to provide peace of mind, while largely ensuring a project can continue even if the original organization or developer packs up their bags, as the source code stays open to be picked up by someone else.
We’re going to highlight two strong open-source candidates. The first is the well-known KeePass.info. Don’t confuse this with the largely defunct KeePassX.org which hasn’t been updated for two years. There is a fork called KeePassXC.org, which is up to date, but we’ll stick with KeePass as it has many unofficial respins for Android and other devices that make it easier to use.
KeePass isn’t as straightforward to use as the commercial alternatives; the main hoop you need to jump through is for multi-device synchronization, where a third-party cloud service, such as Dropbox or Google Drive, needs to be roped in. But the breadth of support, custom options, and feature set is unmatched, with no fees to pay.
The other strong open-source option is Bitwarden. It offers an excellent free model, a $3.33-a-month family subscription that supports up to six users, a basic business version at $5 per month, plus enterprise options. It’s a modern, slick, open-source application supporting macOS, Windows, Linux, all the major browsers—including Opera, Tor, and Brave—plus Android and iOS devices. If you’re a fan of open source, we suggest you give it a look.
This article was originally published in Maximum PC issue 151. For more quality articles about all things PC hardware, you can subscribe to Maximum PC now.
Most Popular


