AMD's Zen 2 chips have a security bug that's getting patched between now and 2024
Zenbleed shouldn't be left exposed for long, so you best keep an eye out for an upcoming AGESA fix for affected chips.
A security vulnerability has been uncovered in AMD processors built with the Zen 2 architecture. Spotted by a Google researcher, the so-called 'Zenbleed' vulnerability opens the door to a potential attacker and threatens the possibility of exposing sensitive information. Don't worry, there is a fix, but us gamers will have to wait around a little longer than our server-side pals to get hold of it.
Zenbleed affects all Zen 2 processors, which includes Ryzen 3000/4000, Threadripper 3000, Ryzen 4000/5000/7020 mobile, and Epyc Rome generations.
The vulnerability, as described by AMD in a security bulletin, occurs "Under specific microarchitectural circumstances, a register in 'Zen 2' CPUs may not be written to 0 correctly. This may cause data from another process and/or thread to be stored in the YMM register, which may allow an attacker to potentially access sensitive information."
The vulnerability is listed as "Medium" severity by AMD, however, its CVE (CVE-2023-20593) is not currently rated.
The vulnerabilities' discoverer, Tavis Ormandy, goes into greater detail on how the exploit works in their blog post. They believe the reason they discovered the bug, as opposed to AMD in post-silicon validation, is because they don't come from an electrical engineering background, oddly enough. They thank a technique called 'fuzzing' for sniffing the bug out, which is a way of testing out weird and unexpected data on a computer to expose unlikely architectural behaviours.
Ormandy notes that the vulnerability would work on your average machine but also virtual machines, sandboxes, containers, processors, "whatever!"
Clearly that's a big deal for large cloud providers, who take security extremely seriously.
The biggest gaming news, reviews and hardware deals
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
Speaking to Tom's Hardware after they first noted the issue, AMD said it was not aware of any actual exploits outside of a research environment. It's certainly appears unlikely that this vulnerability would pose a threat to your average gamer, and it's more the cloud providers that will be worried about potential attacks than you or I, but this is the sort of vulnerability that is best patched up as soon as possible.
AMD was informed of the vulnerability on May 15, 2023, and since then has been working on mitigations.
Mitigations have already begun rolling out for Zenbleed, starting with the affected Epyc chips. We'll see Threadripper chips patched up around October into December, depending on the model. Laptop Ryzen processors should begin being fixed around November/December this year.
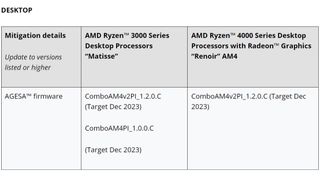
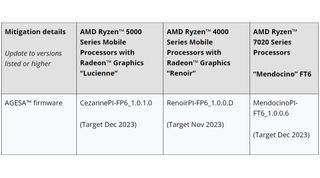
Finally, desktop Ryzen processors will get patched likely around December this year. That's a long time to wait for a patch, but at least this is the sort of mitigation that can be rolled out through microcode and AGESA updates—it wasn't that long ago that hardware mitigations were needed to patch up side-channel attack vulnerabilities on some Intel processors as a result of the Spectre vulnerability, which affected many chips.
Though we haven't yet any idea as to how these patches may affect performance. Mitigations can have an impact, though whether it'll impact gaming isn't known at this time.

Best gaming PC: The top pre-built machines.
Best gaming laptop: Great devices for mobile gaming.
AMD has said to Tom's Hardware: "Any performance impact will vary depending on workload and system configuration."
That's about as vague as it gets on the performance issue, though I wouldn't fret about it just yet. Any performance issues will come out in the wash once the patch drops, and it's possible there's little to no noticeable impact on frame rates
The important thing will be to look out for that new AGESA firmware and get your system secured in case any nefarious ne'er do wells end up trying to take advantage of this exploit. For desktop chips, that's ComboAM4v2PI_1.2.0.C or ComboAM4PI_1.0.0.C.

Jacob earned his first byline writing for his own tech blog. From there, he graduated to professionally breaking things as hardware writer at PCGamesN, and would go on to run the team as hardware editor. He joined PC Gamer's top staff as senior hardware editor before becoming managing editor of the hardware team, and you'll now find him reporting on the latest developments in the technology and gaming industries and testing the newest PC components.
Most Popular





