A new 'browser-in-the-browser' attack threatens Steam users
A sophisticated phishing technique is aimed at competitive gamers.

Receiving a Steam message from someone trying to scam you out of a Team Fortress 2 hat was a rite of passage for PC gamers in the 2010s, but today's phishing techniques are much more sophisticated. The latest attack looks like a real opportunity for up-and-coming competitive gamers, secure login form and all.
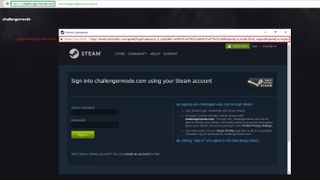
Security firm Group-IB (via Bleeping Computer) says that this sophisticated "browser-in-the-browser" phishing technique appeared "out of nowhere" earlier this year—it was first spotted researcher by mr.d0x—and has been snaring Steam users since. According to the company, the key to the method is that the attackers don't just mimic a webpage, but an entire pop-up browser window. That allows them to make a fake Steam login form look trustworthy by displaying a fake SSL certificate lock symbol and other illusions.
On Steam, the scam's primary targets are competitive and professional gamers, who are being sent direct messages that invite them to join tournaments. If they bite, they're directed to a slick-looking game tournament platform where they're asked to log in using their Steam credentials.
The Steam login pop-up is the fake "browser-in-the-browser" window, and if the user falls for it, the hackers gain access to their Steam account. The prize for the scammers is the account itself and all of the games tied to it, as well as any virtual goods in the user's inventory, such as CS:GO skins. Baiting users with tournament play is perhaps designed to attract competitive gamers who are likely to have expensive items in their Steam inventories, as hardcore CS:GO players can have thousands of dollars worth of skins in their accounts.
The fake pop-up window includes a fake security certificate and supports multiple languages. It can be maximized, minimized, and moved around. Using one's Steam credentials to log into legitimate websites is not uncommon, so some users likely won't think twice about it, given that nothing looks off about the window at first glance.
The attack uses JavaScript, according to Bleeping Computer, so a script blocking extension will offer some protection by preventing the code from running. I use a script blocking extension myself, and although it can be a pain when navigating to new sites, I've found it indispensable.
The general rules of the internet remain: If something appears too good to be true, it probably is. And even if it doesn't appear all that good, it might be even worse that it seems, so don't click on links from sources you don't trust and carefully filter or ignore unknown direct messages and emails. Whether it's cryptocurrency, NFTs, or CS:GO skins, if it has a dollar value attached to it, someone will try to steal it. Stay safe out there!
The biggest gaming news, reviews and hardware deals
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
Best CPU for gaming: Top chips from Intel and AMD
Best gaming motherboard: The right boards
Best graphics card: Your perfect pixel-pusher awaits Best SSD for gaming: Get into the game first

Chris' gaming experiences go back to the mid-nineties when he conned his parents into buying an 'educational PC' that was conveniently overpowered to play Doom and Tie Fighter. He developed a love of extreme overclocking that destroyed his savings despite the cheaper hardware on offer via his job at a PC store. To afford more LN2 he began moonlighting as a reviewer for VR-Zone before jumping the fence to work for MSI Australia. Since then, he's gone back to journalism, enthusiastically reviewing the latest and greatest components for PC & Tech Authority, PC Powerplay and currently Australian Personal Computer magazine and PC Gamer. Chris still puts far too many hours into Borderlands 3, always striving to become a more efficient killer.
Most Popular







